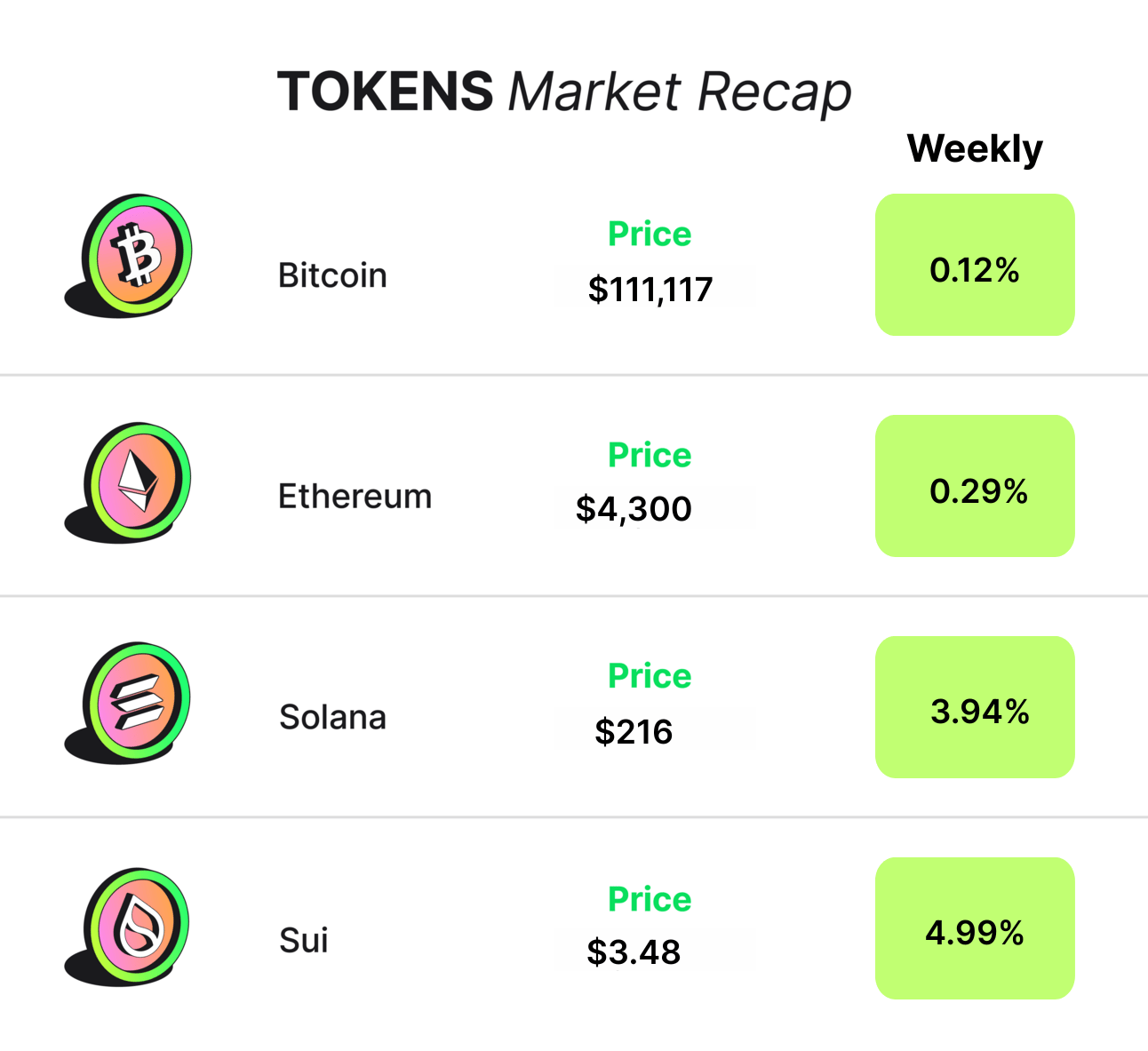
- TOKENS by Crypto Endevr
- Posts
- $2 Billion Blockchain Attack That Stole Only $505
$2 Billion Blockchain Attack That Stole Only $505

This Week on CRYPTO ENDEVR:
Overarching blockchain security was tested by one of the largest software attacks in history, yet the outcome tells a remarkable story about how crypto security has improved. On September 8th, attackers compromised 18 popular software tools with a combined 2 billion weekly downloads, deploying malicious code designed to steal cryptocurrency across multiple networks. Despite the massive scale and potential for catastrophic losses, the attack yielded less than $505 in stolen cryptocurrency, a testament to both rapid community response and the effectiveness of hardware wallet adoption.
This disconnect between potential damage and actual losses reveals critical insights about modern crypto security practices that every investor, developer, and institution should understand.
Taken 9:15pm EST 9/9/25

Anatomy of a Failed Heist
Attackers launched their operation through a sophisticated email scam targeting developer Josh Junon, who maintains several critical software tools used by millions of websites and applications. Using an advanced phishing technique, attackers tricked him into revealing his login credentials and security codes, giving them control over software that powers everything from basic websites to cryptocurrency wallets.
The malicious code worked in two ways:
Background monitoring - Quietly watching for cryptocurrency transactions to swap wallet addresses with similar-looking attacker addresses
Direct wallet interference - Detecting popular wallets like MetaMask and changing transaction destinations before users could approve them
This theft software targeted six major cryptocurrency networks: Bitcoin, Ethereum, Solana, Tron, Litecoin, and Bitcoin Cash. Instead of trying to steal users' private keys or recovery phrases directly, the attackers used a sneakier approach. They waited for people to start sending cryptocurrency, then swapped out the recipient's address with their own wallet address at the last second.
However, the attackers made serious mistakes in their code. The malicious software had bugs that caused systems to crash and display error messages, immediately alerting developers and security companies that something was wrong. What should have been a silent, devastating attack instead became obvious very quickly, triggering an immediate response from the crypto community.
Update on the NPM attack: The attack fortunately failed, with almost no victims.🔒
It began with a phishing email from a fake npm support domain that stole credentials and gave attackers access to publish malicious package updates. The injected code targeted web crypto activity,
— Charles Guillemet (@P3b7_)
8:47 AM • Sep 9, 2025

Why Hardware Wallets Proved Bulletproof
Minimal financial impact of just $505 across all targeted networks demonstrates the real-world effectiveness of hardware wallet adoption and security best practices within the crypto community. Major wallet providers, exchanges, and apps including MetaMask, Ledger, and Uniswap reported no significant compromises, primarily due to robust security features.
Hardware wallets created an impenetrable barrier because:
Transaction verification happens offline - Users physically confirm transaction details on device screens, making address swaps immediately visible
Private key protection - Private keys never touch potentially compromised computer environments
Multi-step confirmation - Hardware wallets require explicit user approval for each transaction component
Limited success came primarily from smaller cryptocurrency transfers and low-value transactions, suggesting that victims may have been using software wallets or engaging in rapid trading without careful verification. Security firms including Aikido Security, SEAL, and Arkham Intelligence tracked attacker wallets in real-time, confirming that major institutional flows and high-value transactions remained completely unaffected.
This outcome validates crypto industry's multi-year push toward hardware wallet adoption, particularly for institutions and serious investors. Essentially, this attack served as a live stress test of security practices, with hardware wallets emerging as clear defensive winners.
Not all hardware wallets are equal.
Clear signing provides an additional layer of security that we recommend to everyone.
Lets get into it🧵
— Ledger (@Ledger)
12:46 PM • Sep 8, 2025

Developer Security Lessons and Industry Response
This software attack exposed critical vulnerabilities in open-source code management while showcasing crypto community's impressive response capabilities. Detection occurred within 2.5 hours of malicious code going live, primarily due to automated monitoring systems and developer vigilance rather than user reports of stolen funds.
Key security practices that limited damage:
Version locking - Many production systems use fixed software versions, preventing automatic malicious updates
Automated monitoring - Security firms like Aikido Security maintain threat detection systems that spotted problems immediately
Community alerting - Ledger CTO Charles Guillemet's warning post reached 8.5 million views, rapidly spreading awareness
For developers building in the crypto space, this incident provides a crucial security lesson. Projects should regularly scan their code for problems, use secure software installation methods, and monitor their systems for unexpected changes. This attack has created new warning signs that security tools can now watch for, helping prevent similar incidents in the future.
Broader crypto development community responded with impressive coordination, sharing detection methods and protection strategies across platforms. This collective response capability represents significant progress in crypto security infrastructure, moving beyond individual project security toward ecosystem-wide threat intelligence sharing.
ATTACK UPDATE: A massive supply-chain compromise has affected packages with over 2 billion weekly downloads, targeting *CRYPTO*
Here's how it works 👇
1) Injects itself into the browser
Hooks core functions like fetch, XMLHttpRequest, and wallet APIs (window.ethereum, Solana,
— Aikido Security (@AikidoSecurity)
3:24 PM • Sep 8, 2025
Security Maturation Signal
This software attack of September 2025 will likely be remembered not for its scope, but for its failure to achieve meaningful damage despite unprecedented reach. With 2 billion weekly downloads affected yet only $505 stolen, this incident serves as a powerful demonstration of how far crypto security practices have evolved.
Attack validated three critical security trends: hardware wallet adoption has reached sufficient scale to stop major threats, automated monitoring systems can detect and contain sophisticated attacks within hours, and crypto development community has built robust information sharing networks that enable rapid collective response.
For investors, this incident reinforces fundamental importance of hardware wallet usage and proper transaction verification practices. For developers, it highlights necessity of comprehensive software security measures and code management protocols. For broader crypto industry, it demonstrates that security infrastructure investments are paying tangible dividends when faced with real-world threats.
As crypto adoption continues expanding into mainstream applications and institutional portfolios, this type of rapid threat containment and minimal actual damage provides confidence that industry security foundations are solid, even when facing attacks at unprecedented scale.

👉 Enjoyed this issue? Don’t keep it to yourself—share the knowledge! 📤 Forward this newsletter to your friends and share your favorite takeaways on social media with #TokensNewsletter!
UNBOUND: Founders Edition
This week on our Founders Space Spotlight, we sat down with Aslan, a key developer in the Sui DeFi ecosystem who's been at the forefront of building collaborative, secure protocols. From his insights on why the Sui ecosystem fosters unprecedented collaboration among projects to his practical advice for aspiring builders ("ship an MVP, post about it, don't be afraid to DM people"), Aslan shared the mindset that's driving the next generation of crypto infrastructure. Whether you're a developer looking to break into crypto or an investor wanting to understand what separates strong ecosystems from the rest, this conversation reveals why building relationships and shipping products matter more than perfect plans.
Click the picture below to hear the full Spaces!
Crypto Endevr is always on the lookout for the latest news and trends in the world of blockchain technology, but it’s not possible without you. Thank you for your support. We look forward to navigating the crypto landscape together in 2025 and beyond!

This content is for informational purposes only and does not constitute financial advice. Always conduct your own research before making investment decisions.

